My 3-2-1+ Backup Strategy

After my recent encounter with malware that nearly compromised my system (as shared in this LinkedIn post), I've decided to outline my backup strategy. This approach has proven invaluable during security incidents and could serve as a template for your own data protection plan.
The Hard Truth About Data Loss
When malware struck my system through what appeared to be a legitimate GitHub repository, I was faced with a stark choice: wipe everything or risk persistent compromise. Thanks to my comprehensive backup system, I could confidently wipe my Mac and restore from a clean Time Machine backup without losing valuable data.
Without proper backups, I would have faced:
- Loss of client work and projects
- Compromised personal data
- Extensive downtime rebuilding my development environment
- Potential permanent loss of irreplaceable files
The 3-2-1+ Backup Strategy Explained
My system follows the classic 3-2-1 backup strategy with additional safeguards:
3: Maintain at least THREE copies of important data
- Primary copy (on your working device)
- Local backup (NAS, external drive)
- Off-site backup (cloud storage, remote location)
2: Use at least TWO different storage types
- Different media types (SSD, HDD, optical media)
- Different backup mechanisms (Time Machine, sync software, manual backups)
1: Keep at least ONE copy off-site
- Cloud storage (Wasabi S3, Google Drive, Dropbox)
- Physical backup in another location (e.g. family member's home or a safety deposit box)
+: Additional protections
- Automated verification of backups
- Regular testing of restoration processes
- Encrypted storage for sensitive data
- Air-gapped storage for critical information
My Actual Implementation
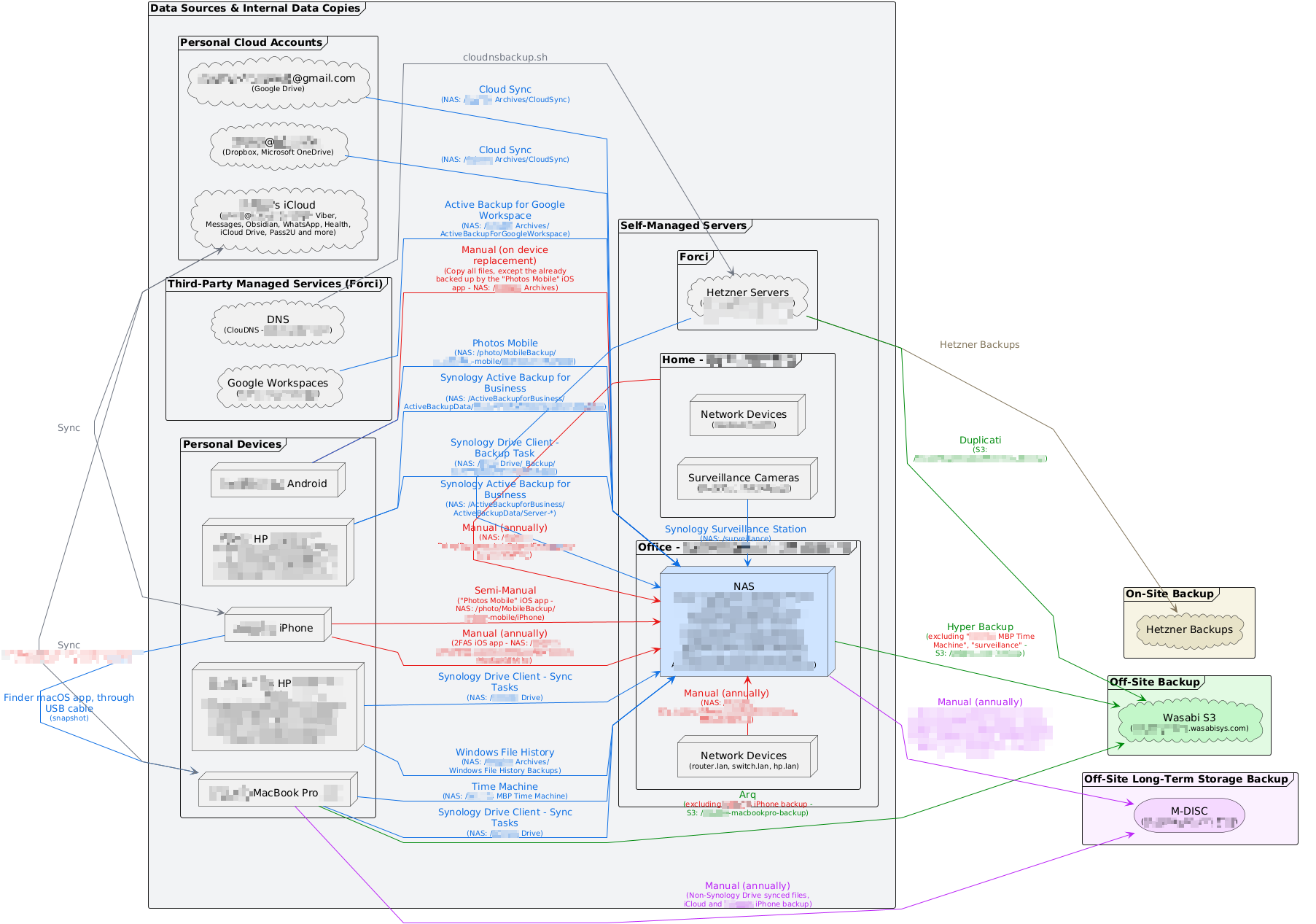
Zoom in to explore the diagram. The color-coding indicates different backup types: red lines for manual processes requiring human intervention, blue lines for automated backups, green paths for off-site backups, and purple for long-term archival storage.
Here's how I've implemented this strategy across personal and business data:
Local Device Backups
- Mac: Time Machine backups to Synology NAS (automatic, hourly)
- iPhone: iCloud backup + manual critical data export (2FA app data)
- Windows PCs: File History + Synology Drive Client sync tasks
NAS as Central Hub
- Synology NAS with redundant drives (RAID protection)
- Serves as the central repository for all devices
- Runs specialized backup applications:
- Synology Drive for continuous file sync
- Active Backup for Business (Windows PCs and servers)
- Cloud Sync (for cloud storage accounts)
- Photos Mobile for smartphone photos/videos
Off-site Cloud Storage
- Wasabi S3: For business critical data with Hyper Backup
- Cloud accounts: Google Drive, Dropbox, OneDrive with selective sync
- Server backups: Hetzner backups + Duplicati to cloud storage
Long-term Archival Storage
- M-DISC optical media: For truly critical data and annual archiving (read my detailed guide on M-DISC technology)
- Unlike regular optical media which can degrade in 5-10 years, M-DISCs use mineral-based recording layers that manufacturers claim will last 1,000+ years
- Resistant to environmental factors like humidity, heat, and light exposure
- Perfect for "write once, read many times" archival purposes
- Ideal for critical data that rarely changes but must be preserved long-term (family photos, legal documents, encryption keys)
- Provides a truly offline backup immune to ransomware, cloud provider issues, or online attacks
- Can be stored in multiple physical locations for geographic redundancy
Critical Security Data
- Emergency recovery information stored in encrypted containers
- Multiple copies in physically separated locations
- Annual verification and updates
Key Principles That Saved My Data
- Automation wherever possible: Set up automated processes for routine backups
- Annual review and testing: Regularly test restoration and update emergency plans
- Defense in depth: No single point of failure in the backup strategy
- Separation of concerns: Different backup tools for different types of data
Lessons From My Malware Encounter
- Never run dev tools (especially
npm install) on unknown code: Even from seemingly legitimate sources without verification - Have an emergency plan: Know exactly what to restore and how
- Verify backup integrity: A backup is only as good as your ability to restore from it
- Prevention: Isolate unknown code in containers or VMs to limit potential damage
- Be ruthless with compromised systems: When in doubt, wipe and restore
Project Isolation: A Preventive Measure
One excellent approach to minimize risk is through project isolation using virtual machines. VMware hypervisors are now free, allowing you to create separate stable and performant Windows and macOS desktop environments per project and even clone them from templates. This creates natural containment boundaries - if one environment gets compromised, others remain protected.
This approach is particularly valuable when working with applications that have security concerns:
- Electron-based apps: Many modern applications (like VS Code, Slack, Discord) use the Electron framework, which has had numerous security vulnerabilities due to its Chromium base and Node.js integration
- AI tools: Applications like Cursor that execute code as part of their functionality present unique security challenges and should be isolated when working with untrusted content
Prevention through isolation is significantly better than relying on backup restoration, especially for high-risk activities like running unknown code or using tools with broad system access.
Annual Backup Procedures
For critical data, I've established an annual backup ritual that covers:
- Identifying and backing up all manual (red-marked) connections in my backup diagram
- Preparing M-DISC directories for long-term storage with newly created files
- Updating encrypted emergency containers with current passwords and critical recovery information
- Copying these emergency containers to M-DISC backups to prevent data loss
- Maintaining a list of all M-DISC backups with creation dates and contents
- Verifying the restoration process to ensure recoverability
This structured approach ensures even my most critical data (like two-factor authentication backups, emergency contacts, and encryption keys) remains available while maintaining security.
Emergency Planning: Data Estate Management
Beyond technical backups, I maintain a comprehensive "Data Estate" plan for critical information access and digital asset management in case of incapacitation. This includes detailed instructions for:
- Accessing encrypted containers with recovery passwords
- Managing domain names and website continuity
- Handling financial accounts and digital assets
- Providing step-by-step instructions for designated emergency contacts
My Data Estate document includes clear designations of responsibilities, prioritized tasks, contact information for technical assistants, and inventory of digital assets with access instructions.
At some point in the future, I might write a dedicated article about how to organize such plans in a secure yet accessible way, as this complements any good backup strategy by ensuring your data remains accessible to those who might need it.
Getting Started With Your Own Strategy
- Start small: Even a simple external drive backup is better than nothing
- Build incrementally: Add components as your comfort level grows
- Consider a NAS: A network storage device simplifies centralized backups (check Marius Hosting for excellent Synology NAS tutorials)
- Add cloud storage: For critical off-site protection
- Document your process: Create simple procedures for backup and restoration
- Test your restoration process: Verify everything works before you need it
Experience has shown that a comprehensive backup system is much cheaper when weighed against potentially lost work or memories.
If you have questions or need personalized advice about securing your data, don't hesitate to reach out. I'm always happy to help fellow data guardians protect what matters most. 👊
Want more ideas, insights, or practical guides? Subscribe here for more tips and tricks: